- Published on
Using Cloudflare Zero Trust to expose services
- Authors

- Name
- Tong
Zero Trust Network has been hot these days. It's a new security model for the Internet to replace the old "castle-and-moat" model.
The term "Zero Trust Network" means we don't trust anything by default in a network to have a better security level. So we have to verify everything before we trust it.
I found this part which explains Zero Trust Network very well in the book Project Zero Trust1:
There are many definitions of Zero Trust. NIST defines it as follows (https://doi.org/10.6028/NIST.SP.800-207):
Zero trust (ZT) provides a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised. Zero trust architecture (ZTA) is an enterprise’s cybersecurity plan that utilizes zero trust concepts and encompasses component relationships, workflow planning, and access policies. Therefore, a zero trust enterprise is the network infrastructure (physical and virtual) and operational policies that are in place for an enterprise as a product of a zero trust architecture plan.
I have been using Cloudflare for a long time. Cloudflare has a Zero Trust Network product called Cloudflare One. It's a great product to protect your network and services.2
In this blog post, I'll show you how I exposed SSH and HTTP services from my home to the public by using Cloudflare's Zero Trust Network. So I can access these services from anywhere without exposing them to the public.
Cloudflare Zero Trust Authentication
Cloudflare Zero Trust Authentication supports many authentication methods. I use Cloudflare Access to protect my services.
This is a screenshot of my Authentication settings:
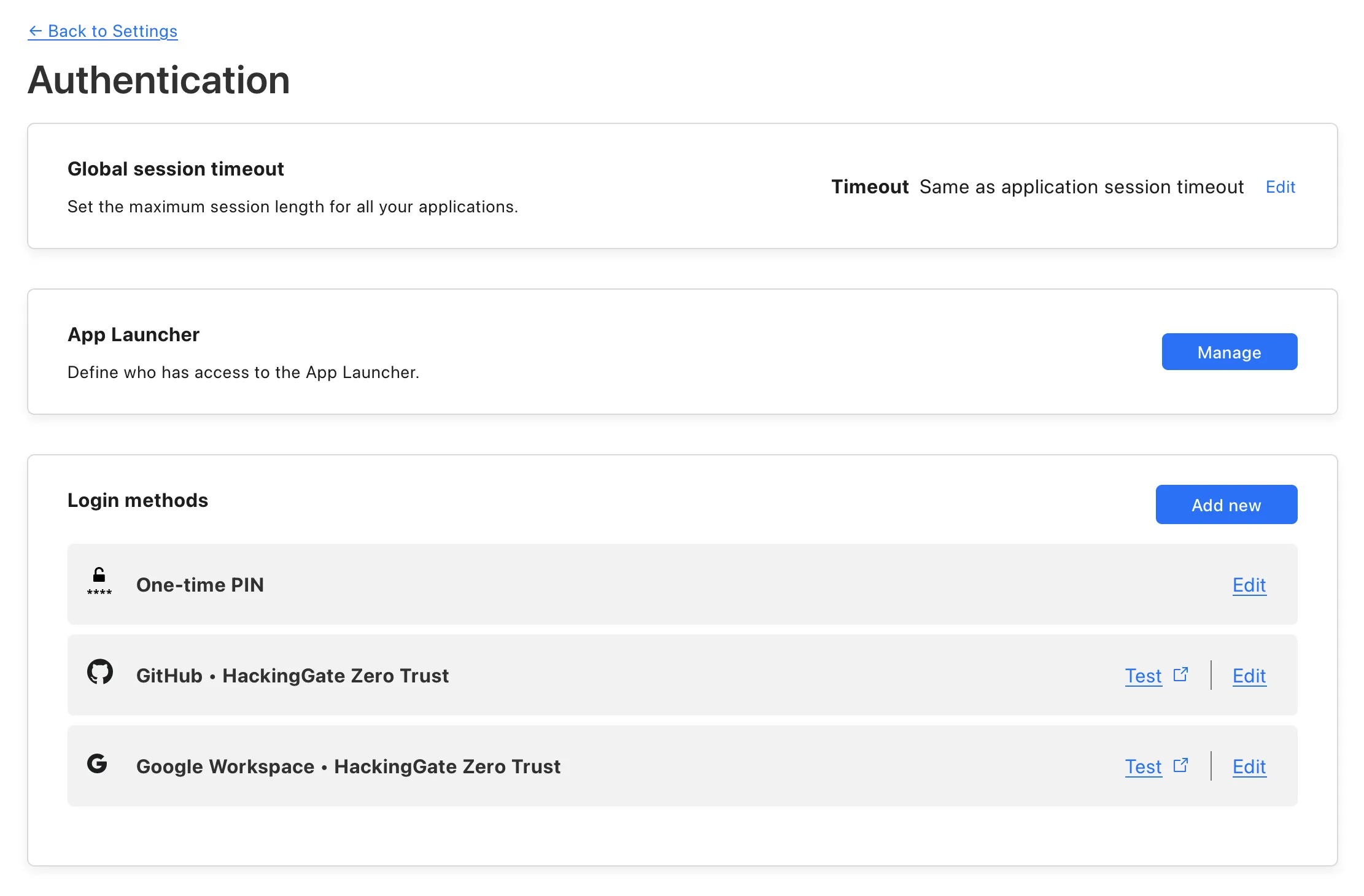
I have three authentication methods:
- One-time PIN (OTP) via email
- GitHub
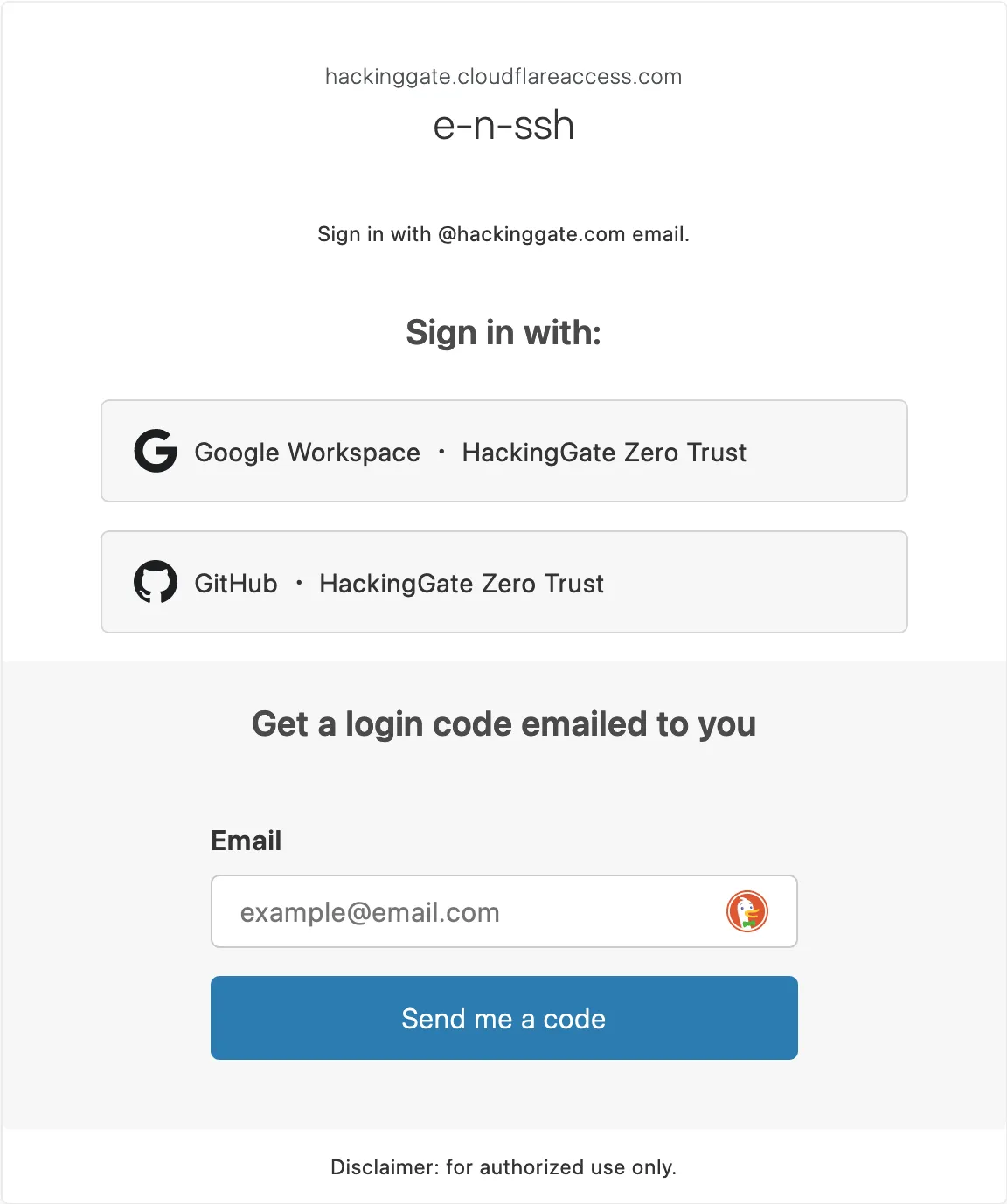
And only members with the email domain hackinggate.com can access my services.
Cloudflare Tunnel
Follow Cloudflare Zero Trust's guide to set up your Cloudflare account and Zero Trust team.
https://developers.cloudflare.com/cloudflare-one/setup/
After creating a Zero Trust team. You can go to Access Tunnels to create tunnels. Cloudflare Zero Trust will generate copy-pastable scripts to let you run tunnels with cloudflared command easily.
After running the tunnel, if you see "HEALTHY" in the status, it means the tunnel is working.
Exposing my Raspberry Pi
I have a Raspberry Pi at home. I want to access it from anywhere. So I created a tunnel for SSH.
Create a tunnel for Raspberry Pi:
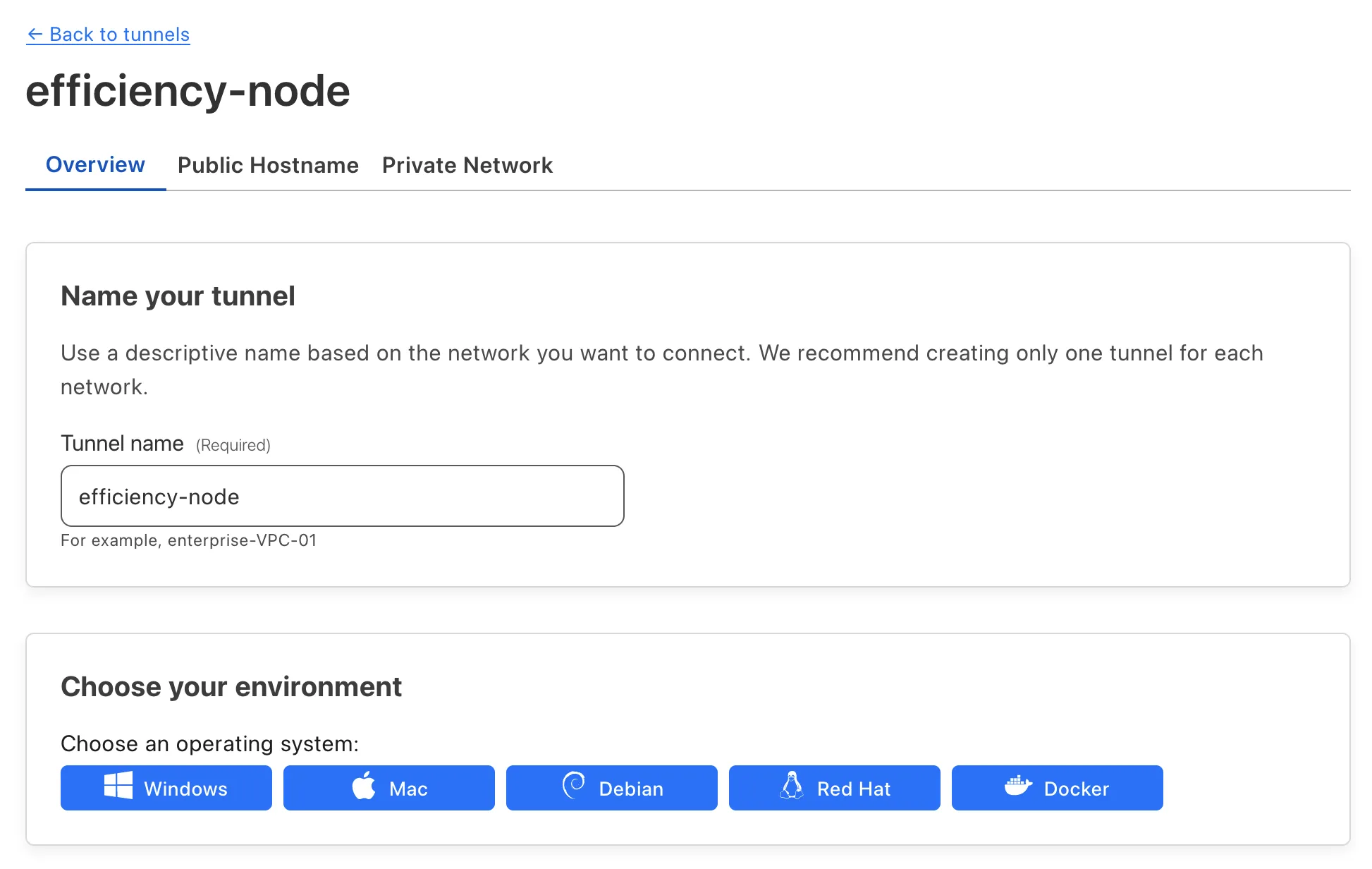
SSH
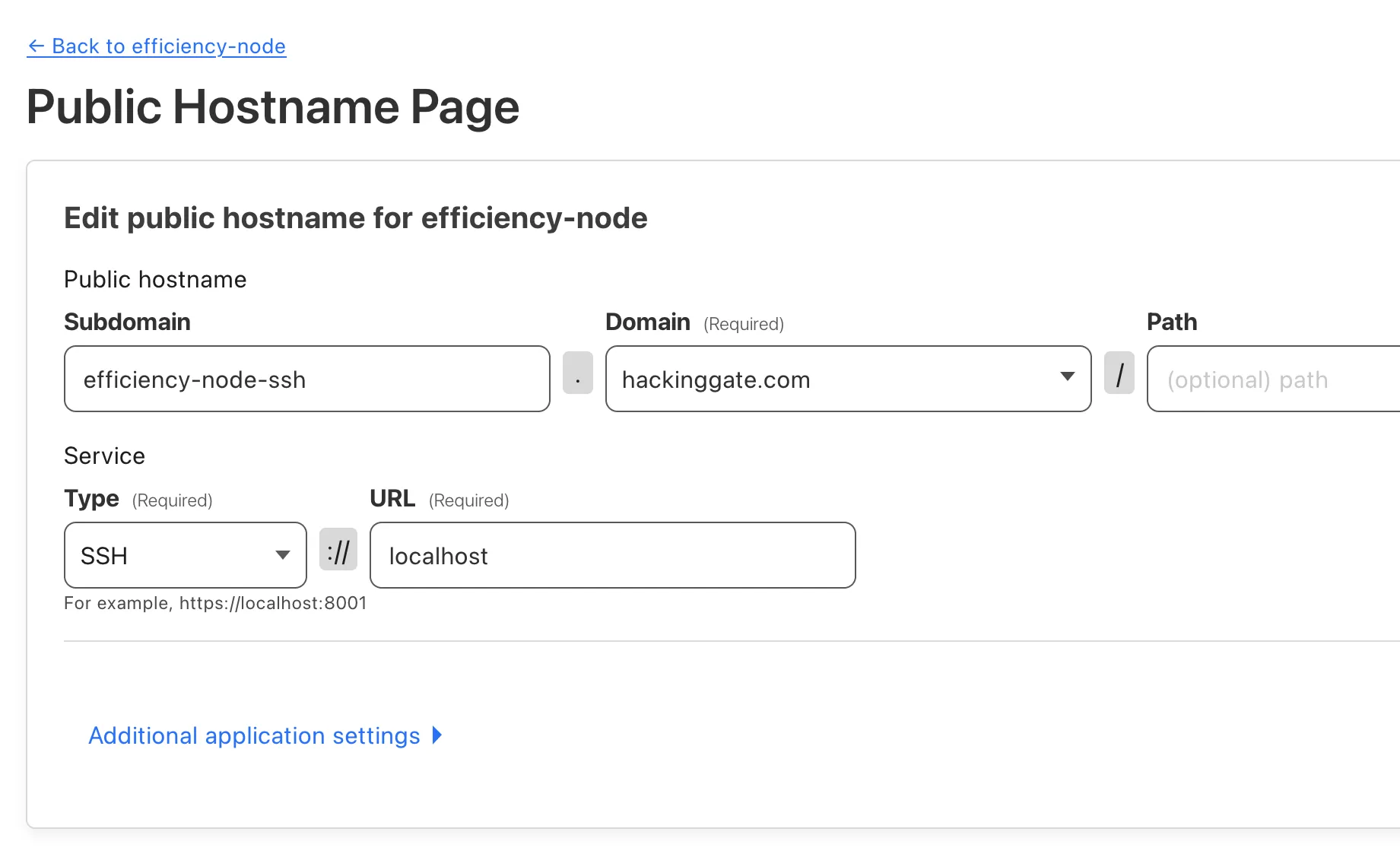
Create an SSH hostname for the tunnel:
I will expose ssh://localhost to ssh://efficiency-node-ssh.hackinggate.com.
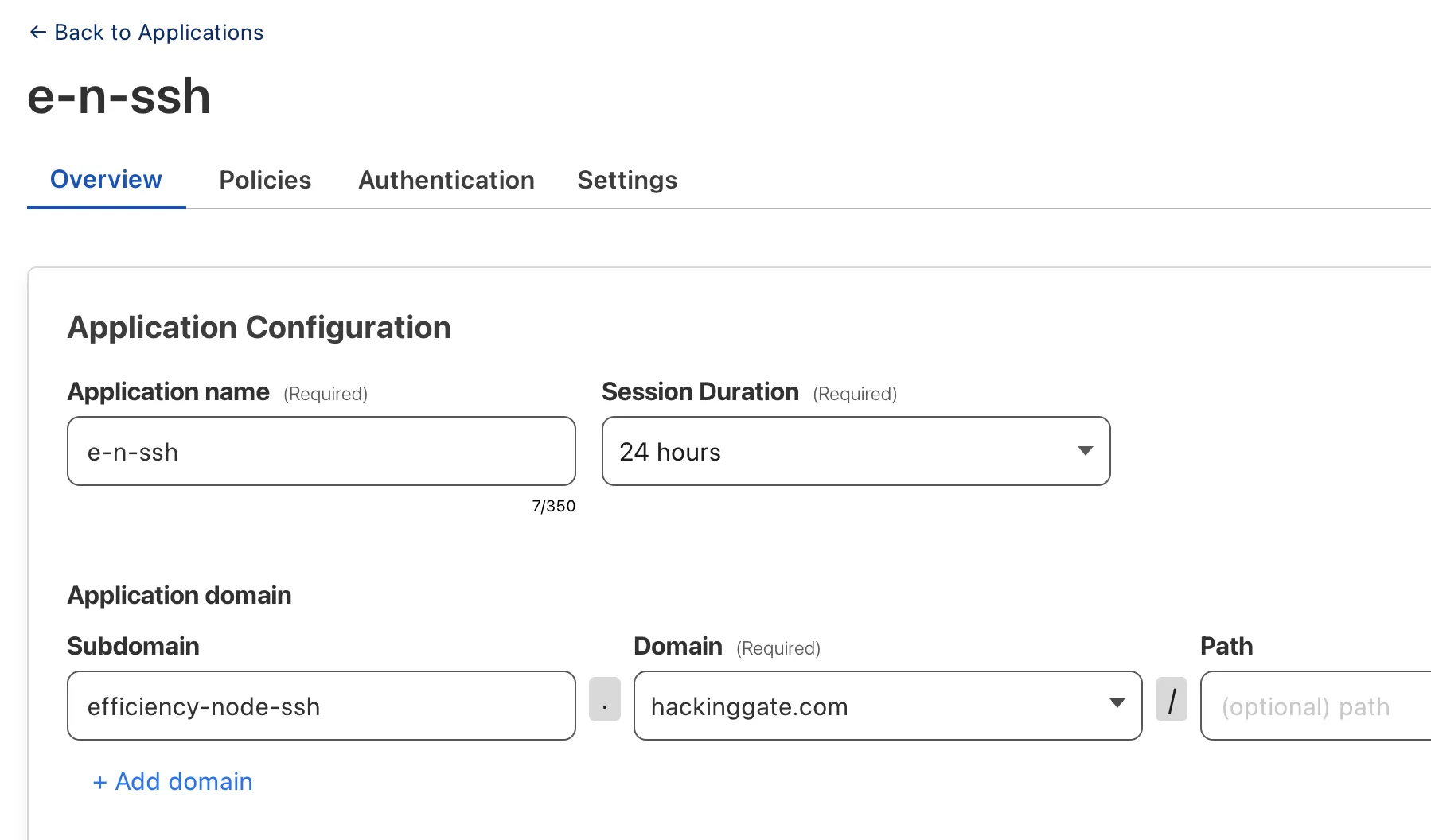
Create an application for SSH service:
Chang .ssh/config to use the tunnel:
Host pi
Hostname efficiency-node-ssh.hackinggate.com
User pi
ProxyCommand /usr/local/bin/cloudflared access ssh --hostname %h
Test the tunnel:
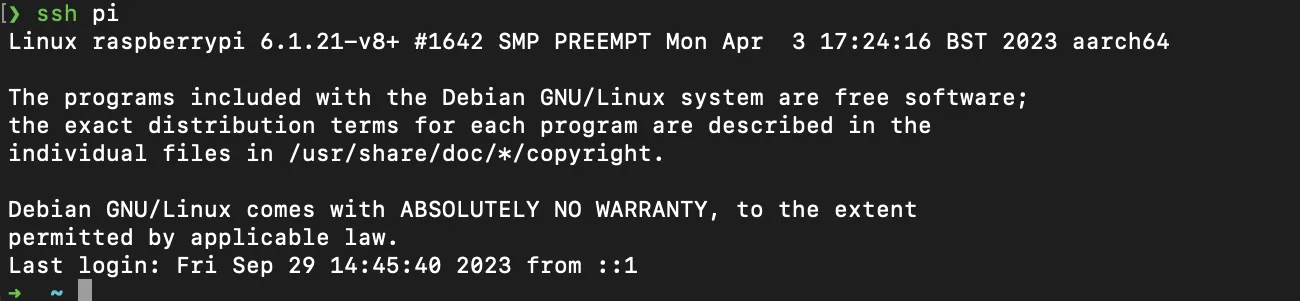
ssh pi
Sign in Cloudflare Access:
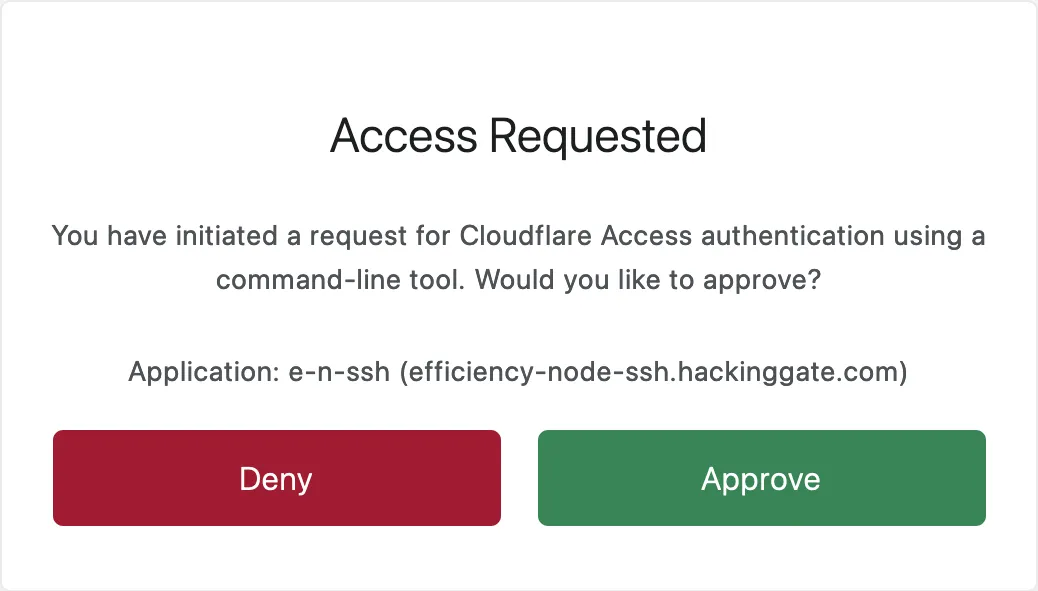
Approve the SSH connection:
It works!
HTTP
Create a HTTP hostname for the tunnel:
I will expose http://localhost:8083 to https://efficiency-node-http.hackinggate.com.
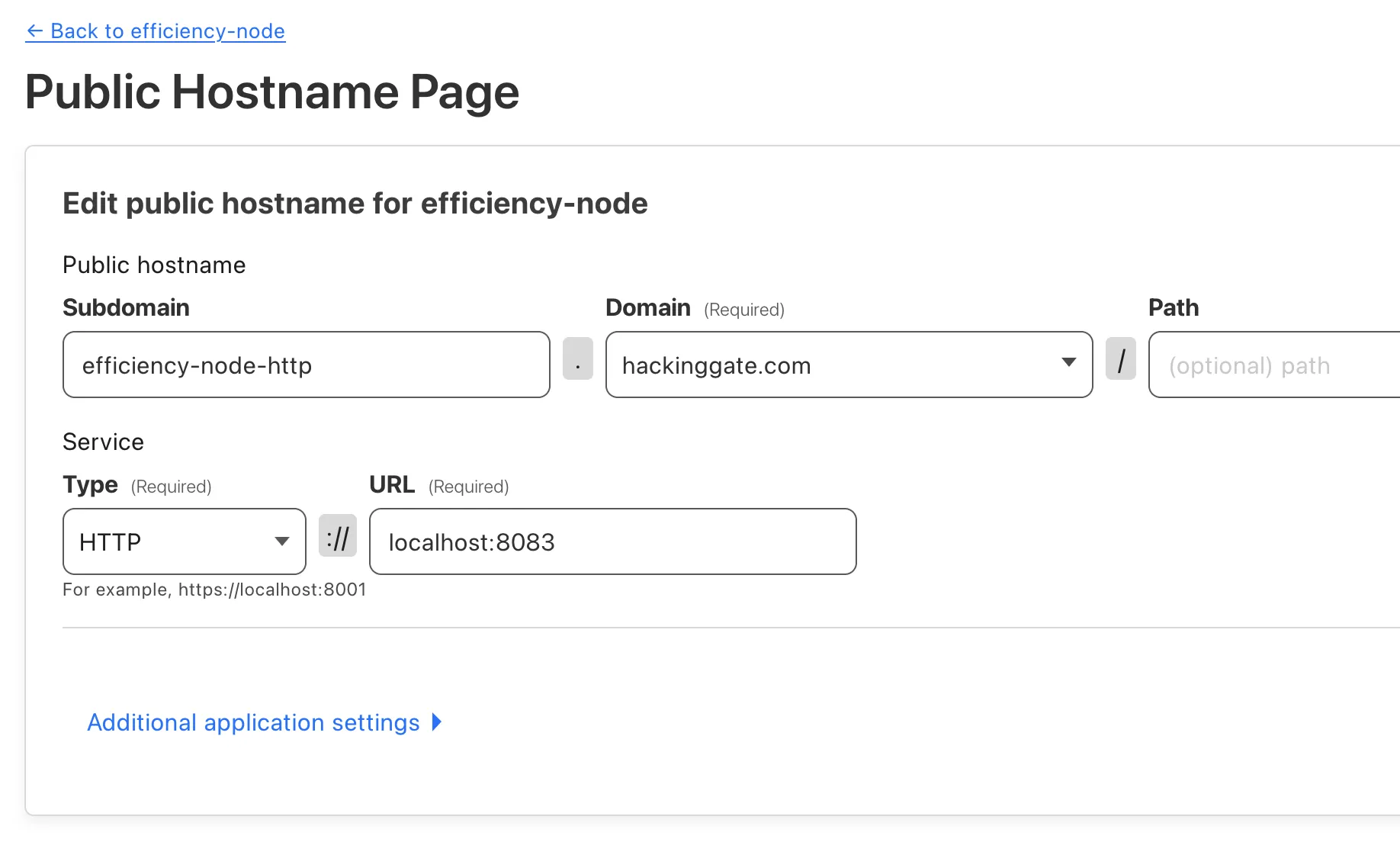
Create an application for HTTP service:
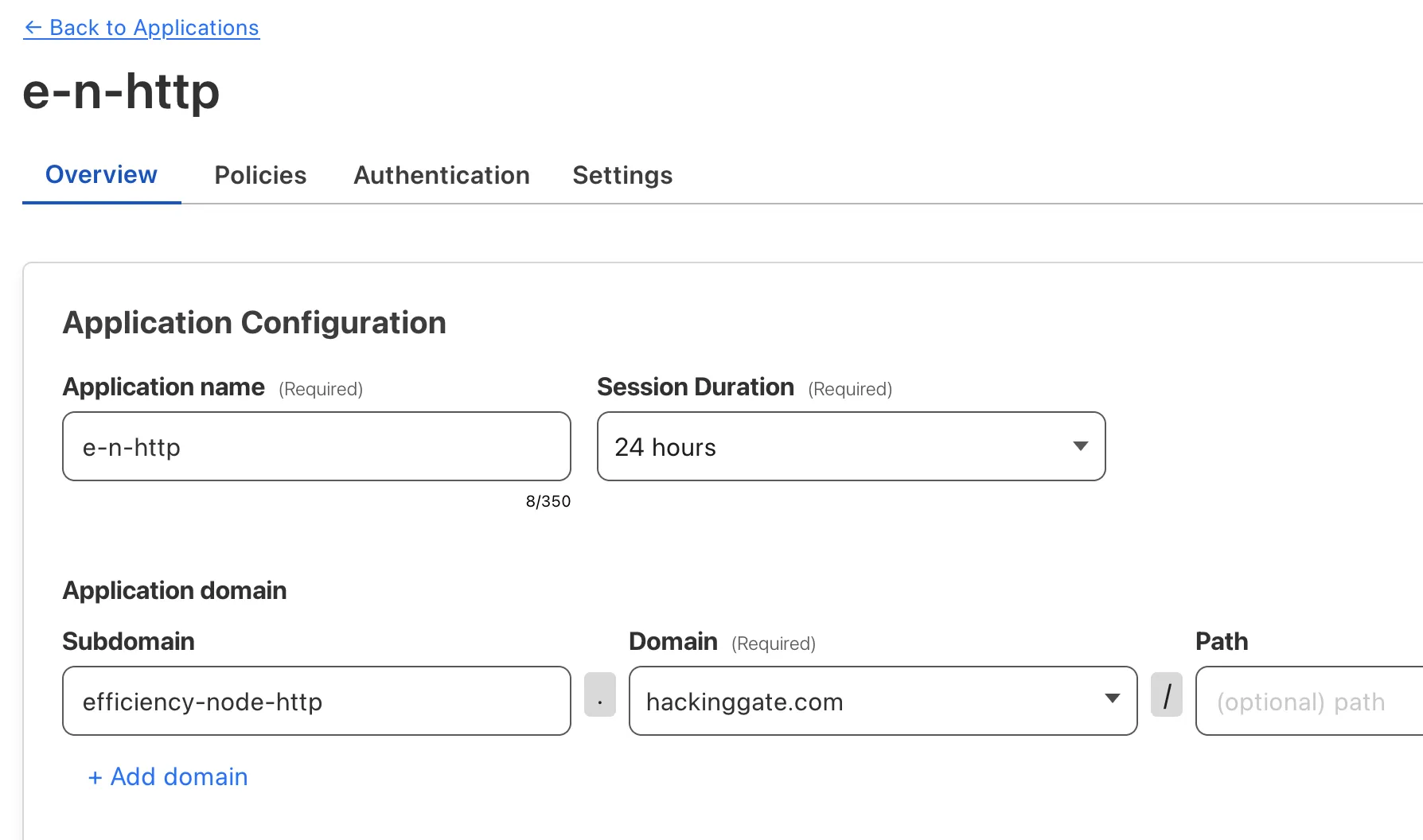
Cloudflare Access
If you enabled app launcher, you can see the application in the app launcher:
Conclusion
Cloudflare Zero Trust is a great product. It's easy to use and has many features. I hope you can use it to protect your network and services.
Footnotes
Project Zero Trust is a book that uses a story-telling way to explain Zero Trust, and it's easy to understand. ↩
You can read more about Cloudflare Zero Trust here: https://developers.cloudflare.com/cloudflare-one/. ↩